A storm has erupted over the theft and black-market sale of the US National Security Agency’s hacking tools. Edward Snowden revealed the widespread use of 'offensive security' tools in 2014. Since then, industry commentators have suggested that the tools and tactics used by the NSA may greatly harm Internet security.
The US is far from alone in possessing such tools. Prime Minister Malcolm Turnbull has said that Australia possesses an “offensive cyber capability” (a capability that the government is seeking to boost). And tonight ABC’s Four Corners will air details of attacks, believed to be state sponsored, allegedly launched by Chinese hackers against a range of Australian networks, including those of Austrade, the Defence Science Technology Group, and the Bureau of Meteorology.
Weaponised hacking tools in the wrong hands could have disastrous consequences. Because the tools are often designed to attack remote computers and servers, a leak of these tools could be catastrophic. Unfortunately, this seems to be exactly what has happened.
In the hands of criminals, hacking tools can be used to attack servers, conduct corporate and government espionage, target company data for identity theft, or create stronger malware and ransomware.
But, what exactly are hacking tools? Why are they such an asset to hackers and the NSA? And, why is the leak of the NSA hacking tools such a threat to the security of the Internet?
Hacking tools target software bugs
Hacking tools work because software is full of bugs. This is true for all software of any reasonable size: Operating systems; web servers; corporate databases; router firmware; even word processing applications — they’re all driven by software, and much of that software has problems and errors.
Unfortunately, many software bugs aren’t easily visible to end-users. These are bugs that occur due to corrupted or malicious data input. While they’re rare, these bugs tend to go unnoticed because they don't affect ordinary software use. As a result, they may exist for years without anyone noticing.
Bugs that create vulnerabilities
While most software bugs are relatively benign (they simply mean the software misbehaves) some bugs in ‘privileged’ applications or even operating systems can create a much bigger issue. These critical bugs may be exploited by hackers to compromise entire computer systems.
Bugs like these are called vulnerabilities, because they make the application or system vulnerable to attack and exploitation. They can range in severity from minor to catastrophic.
A minor vulnerability could allow a hacker to make a server crash, while major vulnerabilities may provide a way to escalate a the hacker's 'privileges' or allow them to bypass all logins. Major vulnerabilities can let a hacker take complete control of a remote system.
A brand new vulnerability that has never been seen before is called a zero-day vulnerability. Luckily, many of these are discovered by security researchers and good hackers who responsibly disclose vulnerabilities to manufacturers before going public. This gives manufacturers enough time to fix problems and release software updates before the flaws are revealed.
Read more: Menlo Security seeks to isolate web-borne threats
Unfortunately, even when manufacturers provide fixes quickly, users often lag behind; they neglect their own maintenance and skip crucial updates. Consequently, servers and networks all over the world are vulnerable to attack.
Consumer-grade hacking tools
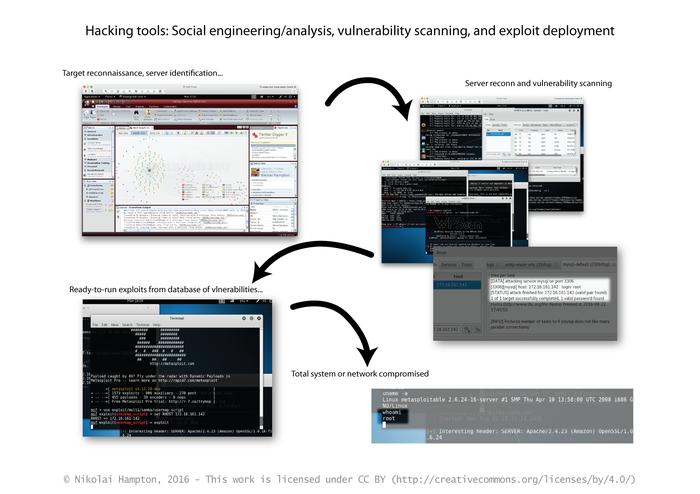
The lag time between the discovery of a zero-day vulnerability, and when computers and servers are fixed, is what allows most hackers to compromise networks. This is where hacking tools come in.Hacking tools are simply collections of known vulnerabilities and software that automate activities such as scanning for unpatched computers and creating malicious data ‘payloads’ to attack systems.
Security researchers and enthusiasts have created many open source hacking tools. Often the tools are used to automate legitimate scanning and testing of network security — it’s common for ‘penetration testers’ and ‘red teams’ to use hacking tools when testing or auditing a network.
While it takes experience, intuition and determination to conduct targeted reconnaissance and breach a system, the tools make it easy enough for unskilled hackers to gain some success in attacking systems. Criminals can also use hacking tool source code to create or improve the destructiveness of malicious software like ransomware, and to create massive ‘dragnet’ style attacks.
Software updates only protect against known attacks
Because many software vulnerabilities are publicly disclosed, the best we can hope for is a timely response from the manufacturers, and that users apply updates as a matter of priority. If updates are applied (in theory) the computer system or network will be safe from any exploits or hacking tools that relied on that specific vulnerability.
Unfortunately, patches can't be made for undisclosed vulnerabilities. The NSA spends considerable effort to test, identify and even purchase zero-day software vulnerabilities. They have no interest in disclosing anything, because that would close the door on their activities. This makes the NSA tools much more powerful and effective than any publicly available tools.
In many cases tools using zero-day vulnerabilities will be impossible to defend against. Imagine a whole box of tools that can be used to attack systems, crack passwords, install monitoring software, break into networks, and compromise routers; with no way of knowing it’s happening or how to defend against it.
The punchline
When powerful ‘weaponised’ hacking tools that use zero-day exploits escape, the possibility for the tools to be used for evil is greatly increased. This is even more likely if the tools are sold for profit on the black-market as seems to be the case with the NSA hacking tools.With these hacking weapons in criminal hands, many Internet businesses and end-users could find themselves hit by serious cyber crime. All we can hope for now, is that the NSA cuts their losses, and works swiftly to help affected software manufacturers patch and update vulnerable systems.
Nikolai Hampton holds a Master's Degree in Cyber Security
and is a director of Impression Research. He consults on matters of privacy,
security, digital forensics, and incident response. His focus is on the correct
application of cryptography. He is passionate about educating business on
complex security issues. Follow Nikolai on Twitter:
@NikolaiHampton

