Researchers have uncovered an invitation-only Tor-concealed marketplace where stolen credit card details are bundled with the victim's device fingerprint, meaning criminal buyers can use them to beat numerous fraud detection systems.
The Genesis Store is currently selling up to 60,000 stolen profile packages – which include browser fingerprints, website user logins and passwords, cookies and credit card information – for between US$5 and $2,000.
Buyers can shop for profiles with a search panel that allows them to filter for logins and passwords from particular websites, the victim’s country, operating system or date the profile first appeared at the darknet market.
"It's a little package the bad guy buys and now he's you," Kaspersky senior security researcher Sergey Lozhkin told Computerworld at the company's Security Analyst Summit in Singapore this week.
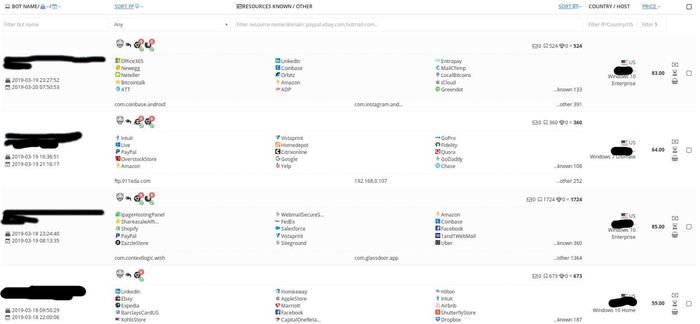
The potential damage is significant. To separate fraudsters from legitimate online shoppers, anti-fraud systems typically use mechanisms to verify the shopper’s digital fingerprint. This 'fingerprint' can include more than 100 attributes from the users device including: IP address (external and local), screen information (such as screen resolution, window size), firmware version, operating system version, browser plugins installed, timezone and so on.
If a card is used to make from the same device (with the same fingerprint) as in the past, the transaction will not raise any red flags.
"As a result, the user behind the mask is recognised to be a legitimate one, and his query, such as an attempt to make a purchase using the provided bank card details, will be approved," Lozhkin said.
To make device mimicry easier, the Genesis Store also offers a plug-in (which runs on the Chromium browser) that allows users to install stolen digital profiles into their browser and "with a single mouse click" become the "doppelganger of the victim" Lozhkin explained.

The Genesis Store owners have formed their considerable collection of card details and profiles through their own malware, but also from requesting missing information from botnet owners, Lozhkin explained.
"They buy it from them and resell. They're a reseller," he said.
The store also offers a unique fingerprint generator for buyers who don't want to purchase card details in the bundles. Using unique fingerprints won't always get around anti-fraud systems, but is less suspicious than multiple cards with multiple identities making purchases from a single device.
Lozhkin explained that there were likely many more, "more private" marketplaces operating with a similar approach.
"This one became semi-pubic because it has a lot of information to sell. So the bad guys want more people to know about its existence... It's the tip of the iceberg in terms of marketplaces," he said.
Fortunately for Australian consumers, most ecommerce sites and banks require two-factor authentication to make purchases online. Consumers in the US and Canada, where two-factor authentication is not standard when shopping online with many banks, were most at risk, Lozhkin said.
"In many shops in the US they won't ask anything. But it depends on the bank. The bad guys, they know the banks that don't use the [two-factor authentication] system, so they try to buy only the exact credit card details for those banks," he said.
Two-factor authentication for transactions initiated using a bank card is an "absolute necessity" and the "best solution" Lozhkin – who has himself been a victim of card fraud – said.
"If you go online and buy a laptop, there should be two-factor authentication, and when you then go and buy a bag for that laptop, you should really have it again," he said.
Lozhkin, who previously investigated online card fraud for the Russian Interior Ministry, said he believed fear of losing customers was ultimately the reason some banks hadn't mandated two-factor authentication.
"There are so many people using credit cards, buying things online, for them it would be hard for a bank to force these people to use two-factor authorisation, to teach them how, because they just want to type their credit card information in," he said.
"For the bank maybe it's better to lose money through fraud then spend it educating the customer. They don't want to lose customers."
Last month the Australian Federal Police announced they hard arrested and charged a Sydney man over his alleged role operating a credential selling website.
The author travelled to the Security Analyst Summit as a guest of Kaspersky.

