The Australian Cyber Security Centre (ACSC) has found a large number of unprotected network, database and storage services hosted on Australian Internet Protocol (IP) address ranges.
According to the ACSC, it has received a number of reports about cyber security incidents that could have been prevented.
"The web-facing services reported through the Australian Internet Security Initiative (AISI) are often vulnerable because they have inadequate authentication and access control processes in place," the ACSC said in a statement.
"Malicious actors are known to exploit these types of vulnerable services in order to commit further cyber-attacks such as: ransomware; theft and/or modification of data and intellectual property; business disruption; denial of service attacks; advanced persistent threat (APT) entry into key business sectors and other harmful activities to either the service owner or other interest users."
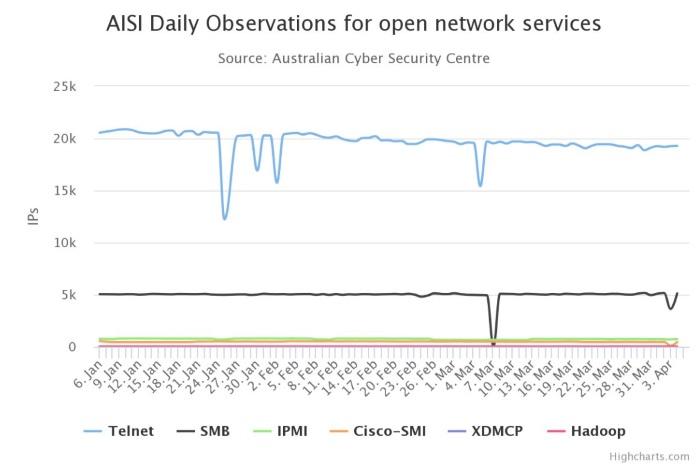
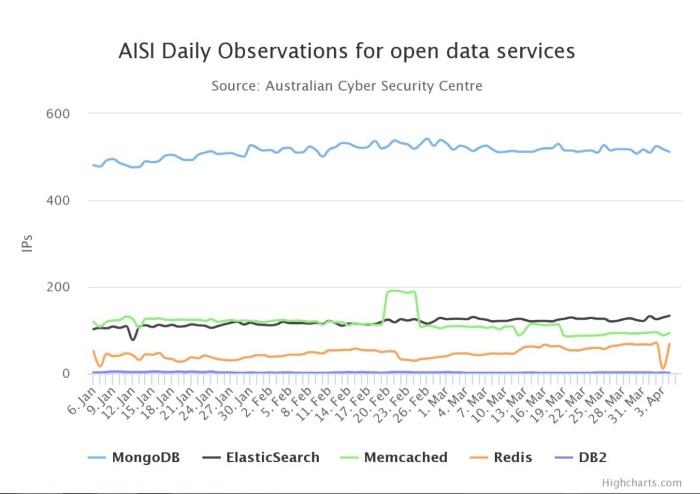
During the first quarter of 2019, the ACSC identified key vulnerable services including MongoDB, ElasticSearch, Telnet and Cisco –SMI.
In 4 March, several reports surged of MongoDB databases that were exposed, especially in China, which could've been part of a country-wide surveillance program, according to a report by Bleeping Computer.
Prior to that, ZDnet reported that a Dutch security researcher "stumbled upon the Kremlin's backdoor account that the government had been using to access the servers of local and foreign businesses operating in Russia", found inside "thousands" of MongoDB databases.
The ACSC said that there were around 500 open Mongo databases and 100 ElasticSearch databases detected each day across Australia, while there were around 20,000 open network services that were potentially vulnerable to exploitation.
"All Australian businesses and organisations should ensure they have implemented strong user authentication and access controls on their databases and network infrastructure, including across all available environments (i.e. development, test, staging, pre-production and production)," it said.
The ACSC has a set of recommendations for businesses here, these include review product vendors’ security guidelines for AWS S3, MongoDB, RedisDB2, ElasticSearch, Memcached, Hadoop, Cisco-SMI and contact the product vendor for relevant security documentation for services other that the ones listed.