Check Point finds ultrasound machine trivial to hack
- 08 March, 2019 10:28
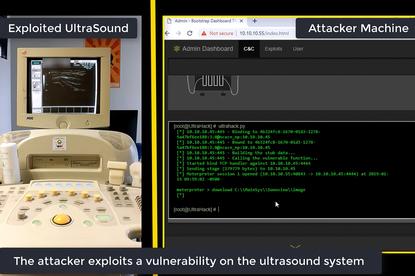
Check Point has warned that medical devices used by major healthcare providers could have gaping security holes, with researchers at the security firm revealing they were able to easily hack an ultrasound machine and retrieve and alter records stored on it.
Although ultrasound technology has “made huge advancements over recent years,” that hasn’t extended to their security, a Check Point blog entry said.
The device obtained by the researchers was based on Windows 2000 — extended support for the Microsoft operating system, which launched in early 2000, ended in July 2010.
Check Point was able not only able to access patient images stored on the machine but also alter the information displayed as well as infect it with ransomware thanks to a known Windows 2000 vulnerability.
Last month a Melbourne Heart Group clinic was reportedly the victim of ransomware, with the medical files of up to 15,000 patients affected.
In the final quarter of 2018 health service providers were responsible for reporting the highest number of data breaches to the Office of the Australian Information Commissioner.
The latest OAIC report on the Notifiable Data Breaches (NDB) scheme reveals that in the period between 1 October and 31 December, health service providers reported 54 breaches. In 54 per cent of cases the breach notifications related to human error. The remainder of incidents related to “malicious or criminal attacks,” however.
Most of the sector’s notifications to the OAIC involved information relating to 100 or fewer people; however in 14 cases it related to 101-100 people, and in seven cases it affected 1001-5000 individuals. In one incident between 5001 and 10,000 individuals were affected by the breach.
When it came to malicious or criminal attacks, 11 of the 25 notifications involved a “cyber incident,” according to the OAIC report. Of those, 36 per cent involved ransomware while the remainder involved compromised credentials.
A recent report from Check Point noted that ‘Internet of Medical Things’ technologies are “currently exploding” in both numbers and capabilities. However, the company warned that their growing popularity brought with it new security challenges.
“This presents a daunting challenge for cybersecurity professionals,” states the report on the most vulnerable targets in cyber security.
“They must not only protect their own devices, but they must also defend against threats targeting external machines that might connect to their IT networks as a whole.
“The current IoT landscape then can be compared to the early days of the internet, when viruses, worms, and email spam plagued users. Many companies raced to join the internet ‘gold rush’ without necessarily considering the importance of internet security.”
